Since no one else has posted this;
(This site is a service that is selling protection, but very informative)

 unit42.paloaltonetworks.com
unit42.paloaltonetworks.com
Black Basta is ransomware as a service (RaaS) that first emerged in April 2022. However, evidence suggests that it has been in development since February. The Black Basta operator(s) use the double extortion technique, meaning that in addition to encrypting files on the systems of targeted organizations and demanding ransom to make decryption possible, they also maintain a dark web leak site where they threaten to post sensitive information if an organization chooses not to pay ransom.
Black Basta affiliates have been very active deploying Black Basta and extorting organizations since the ransomware first emerged. Although the Black Basta affiliates have only been active for the past couple of months, based on the information posted on their leak site, they have compromised over 75 organizations at the time of this publication. Unit 42 has also worked on several Black Basta incident response cases.
The ransomware is written in C++ and impacts both Windows and Linux operating systems. It encrypts users’ data using a combination of ChaCha20 and RSA-4096, and to speed up the encryption process, the ransomware encrypts in chunks of 64 bytes, with 128 bytes of data remaining unencrypted between the encrypted regions. The faster the ransomware encrypts, the more systems can potentially be compromised before defenses are triggered. It is a key factor affiliates look for when joining a Ransomware-as-a-Service group.
Black Basta is ransomware as a service (RaaS) that leverages double extortion as part of its attacks. The attackers not only execute ransomware but also exfiltrate sensitive data and threaten to release it publicly if the ransom demands are not met. The threat actors behind the ransomware deploy a name-and-shame approach to their victim, where they use a Tor site, Basta News, to list all of the victims who have not paid the ransom.
Although the Black Basta RaaS has only been active for a couple of months, according to its leak site, it had compromised over 75 organizations at the time of this publication. At least 20 victims were posted to its leak site in the first two weeks of the ransomware’s operation, which indicates the group likely is experienced in the ransomware business and has a steady source of initial access.
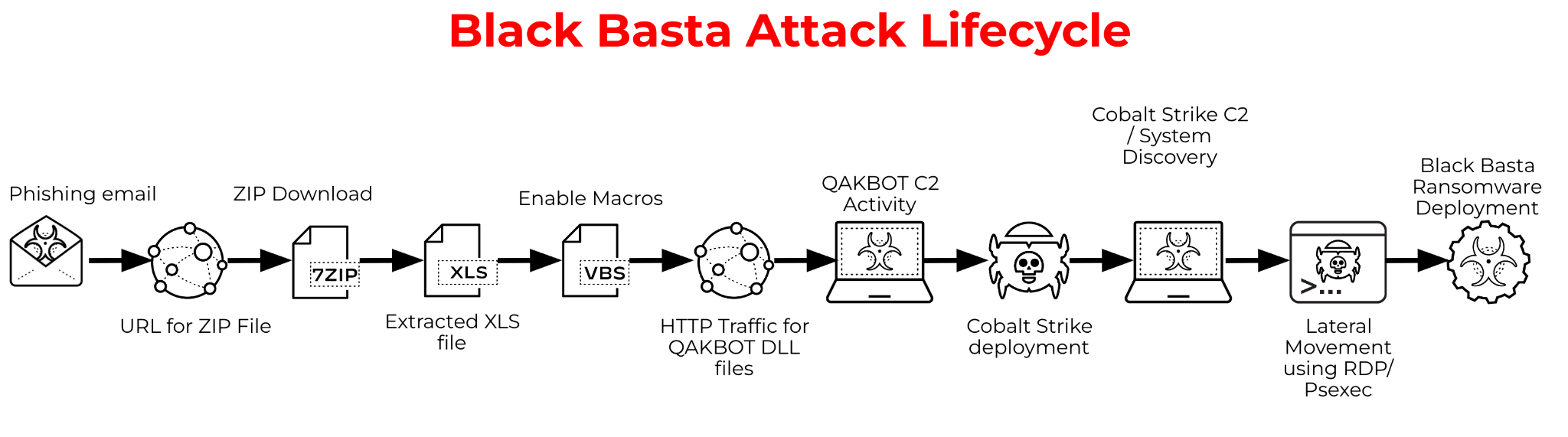
Unit 42 has observed the Black Basta ransomware group using QBot as an initial point of entry and to move laterally in compromised networks. QBot, also known as Qakbot, is a Windows malware strain that started as a banking trojan and evolved into a malware dropper. It has been used by other ransomware groups, including MegaCortex, ProLock, DoppelPaymer and Egregor. While these ransomware groups used QBot for initial access, the Black Basta group was observed using it for both initial access and to spread laterally throughout the network.
(This site is a service that is selling protection, but very informative)

Threat Assessment: Black Basta Ransomware
Black Basta is ransomware as a service (RaaS) that first emerged in April 2022. However, evidence suggests that it has been in development since February. The Black Basta operator(s) use the double extortion technique, meaning that in addition to encrypting files on the systems of targeted...
Black Basta is ransomware as a service (RaaS) that first emerged in April 2022. However, evidence suggests that it has been in development since February. The Black Basta operator(s) use the double extortion technique, meaning that in addition to encrypting files on the systems of targeted organizations and demanding ransom to make decryption possible, they also maintain a dark web leak site where they threaten to post sensitive information if an organization chooses not to pay ransom.
Black Basta affiliates have been very active deploying Black Basta and extorting organizations since the ransomware first emerged. Although the Black Basta affiliates have only been active for the past couple of months, based on the information posted on their leak site, they have compromised over 75 organizations at the time of this publication. Unit 42 has also worked on several Black Basta incident response cases.
The ransomware is written in C++ and impacts both Windows and Linux operating systems. It encrypts users’ data using a combination of ChaCha20 and RSA-4096, and to speed up the encryption process, the ransomware encrypts in chunks of 64 bytes, with 128 bytes of data remaining unencrypted between the encrypted regions. The faster the ransomware encrypts, the more systems can potentially be compromised before defenses are triggered. It is a key factor affiliates look for when joining a Ransomware-as-a-Service group.
Black Basta is ransomware as a service (RaaS) that leverages double extortion as part of its attacks. The attackers not only execute ransomware but also exfiltrate sensitive data and threaten to release it publicly if the ransom demands are not met. The threat actors behind the ransomware deploy a name-and-shame approach to their victim, where they use a Tor site, Basta News, to list all of the victims who have not paid the ransom.
Although the Black Basta RaaS has only been active for a couple of months, according to its leak site, it had compromised over 75 organizations at the time of this publication. At least 20 victims were posted to its leak site in the first two weeks of the ransomware’s operation, which indicates the group likely is experienced in the ransomware business and has a steady source of initial access.
Unit 42 has observed the Black Basta ransomware group using QBot as an initial point of entry and to move laterally in compromised networks. QBot, also known as Qakbot, is a Windows malware strain that started as a banking trojan and evolved into a malware dropper. It has been used by other ransomware groups, including MegaCortex, ProLock, DoppelPaymer and Egregor. While these ransomware groups used QBot for initial access, the Black Basta group was observed using it for both initial access and to spread laterally throughout the network.


